Improved malware scanner now available
Good news: our opensource malware scanner "mwscan" has been succeeded by a much better one called eComscan. It is developed by Sansec, experts in Magento store security.
Update 2021: Sansec is now recognized as Adobe partner and runs on more than 7000 stores worldwide
Use one month free of charge
eComscan offers many improvements over mwscan:
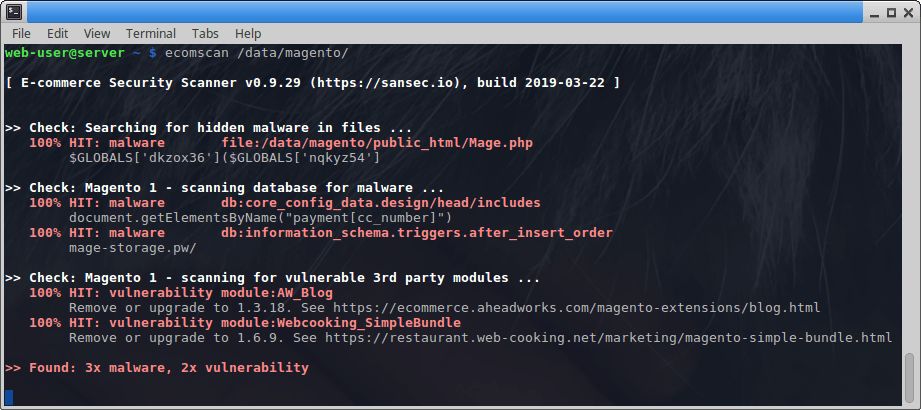
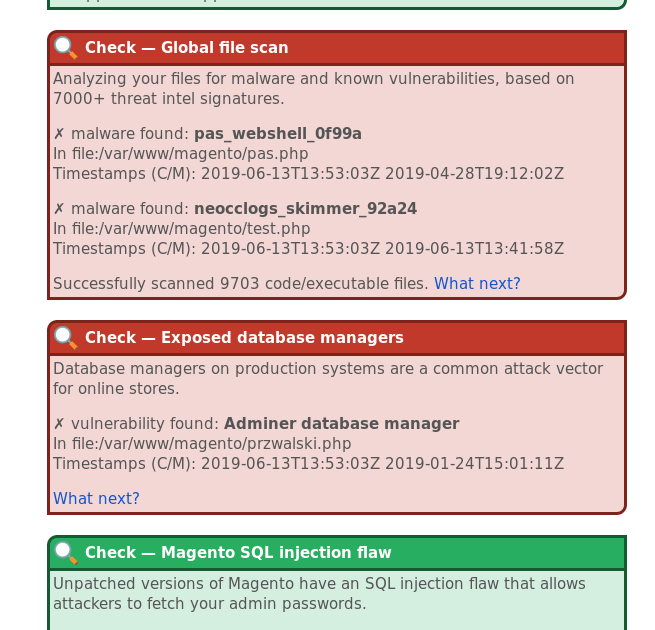
- 22 thousand malware signatures and counting
- Detects vulnerabilities in Magento and third party ecommerce components
- Monitoring of files & databases
- Get instant, actionable alerts via mail, Slack, phone & webhook
The Sansec threat intel team investigates hundreds of hacked stores per month, and adds new attack signatures multiple times per day. We believe it is by far the best solution to protect your Magento store from emerging threats.
You can use our full solution one month free of charge. Get your copy here and and use coupon code MWSCAN. Your store and your customers will benefit!
Sample command line scan
Sample report
Who uses it?
Mwscan and its successor eComscan are recommended by Magento and used by the US Department of Homeland Security, the Magento Marketplace, Magereport, the Mage Security Council and many others.
About payment skimming and Magecart
Online payment skimming (aka "MageCart") is a growing threat to digital stores. Since our first publication in 2015, we identified more than 40.000 compromised stores. In most cases, malware is inserted that will a) intercept customer data, b) divert payments or c) uses your customers for cryptojacking.
Privacy watchdogs and online regulators are increasingly handing out fines to companies who suffered a Magecart attack.