MISP - Threat Intelligence Sharing Platform
| Latest Release | |
| CI Action | |
| Gitter | |
 |
|
| Localization | |
| Contributors |  |
| License |  |
MISP is an open source software solution for collecting, storing, distributing and sharing cyber security indicators and threats about cyber security incidents analysis and malware analysis. MISP is designed by and for incident analysts, security and ICT professionals or malware reversers to support their day-to-day operations to share structured information efficiently.
The objective of MISP is to foster the sharing of structured information within the security community and abroad. MISP provides functionalities to support the exchange of information but also the consumption of said information by Network Intrusion Detection Systems (NIDS), LIDS but also log analysis tools, SIEMs.
MISP, Malware Information Sharing Platform and Threat Sharing, core functionalities are:
- An efficient IOC and indicators database allowing to store technical and non-technical information about malware samples, incidents, attackers and intelligence.
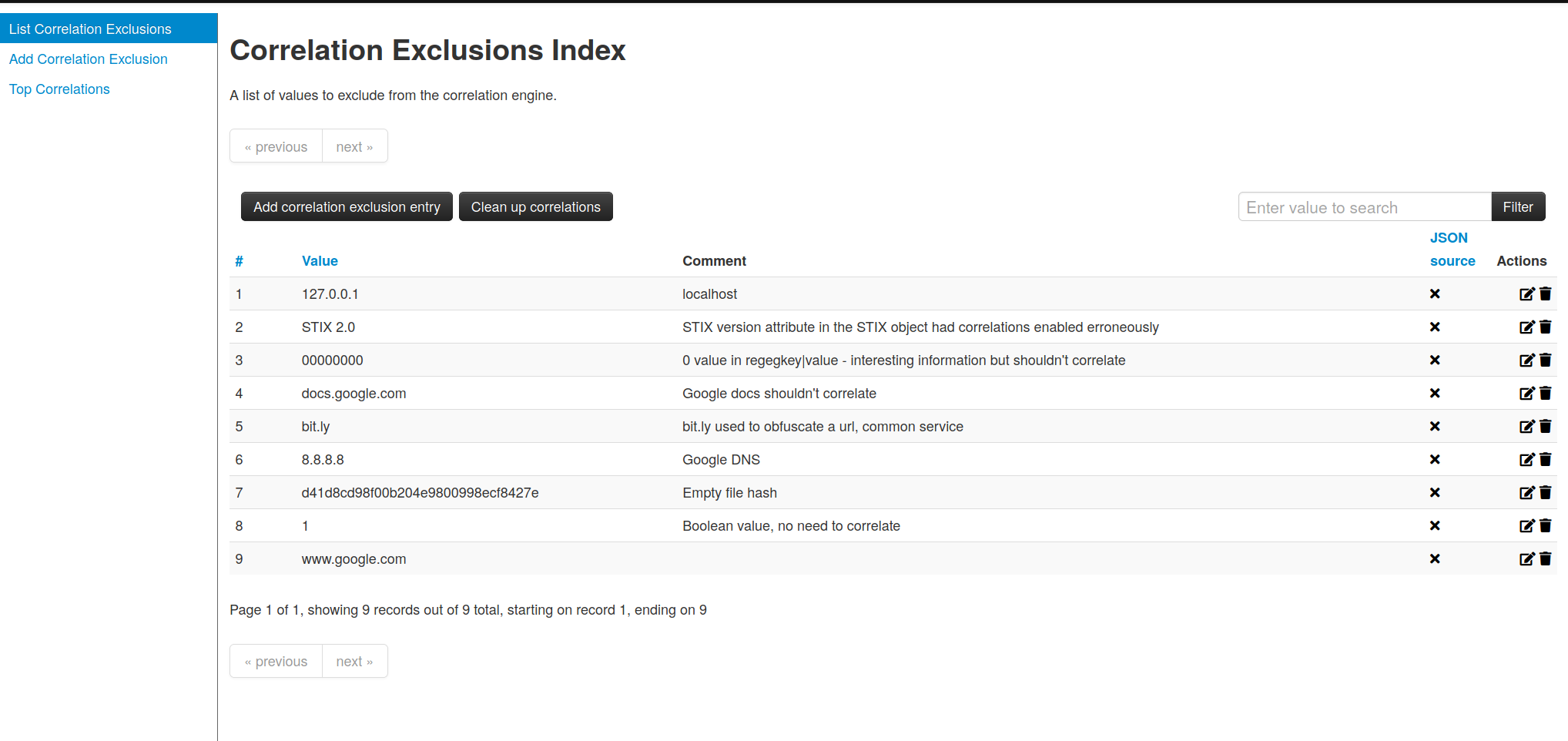
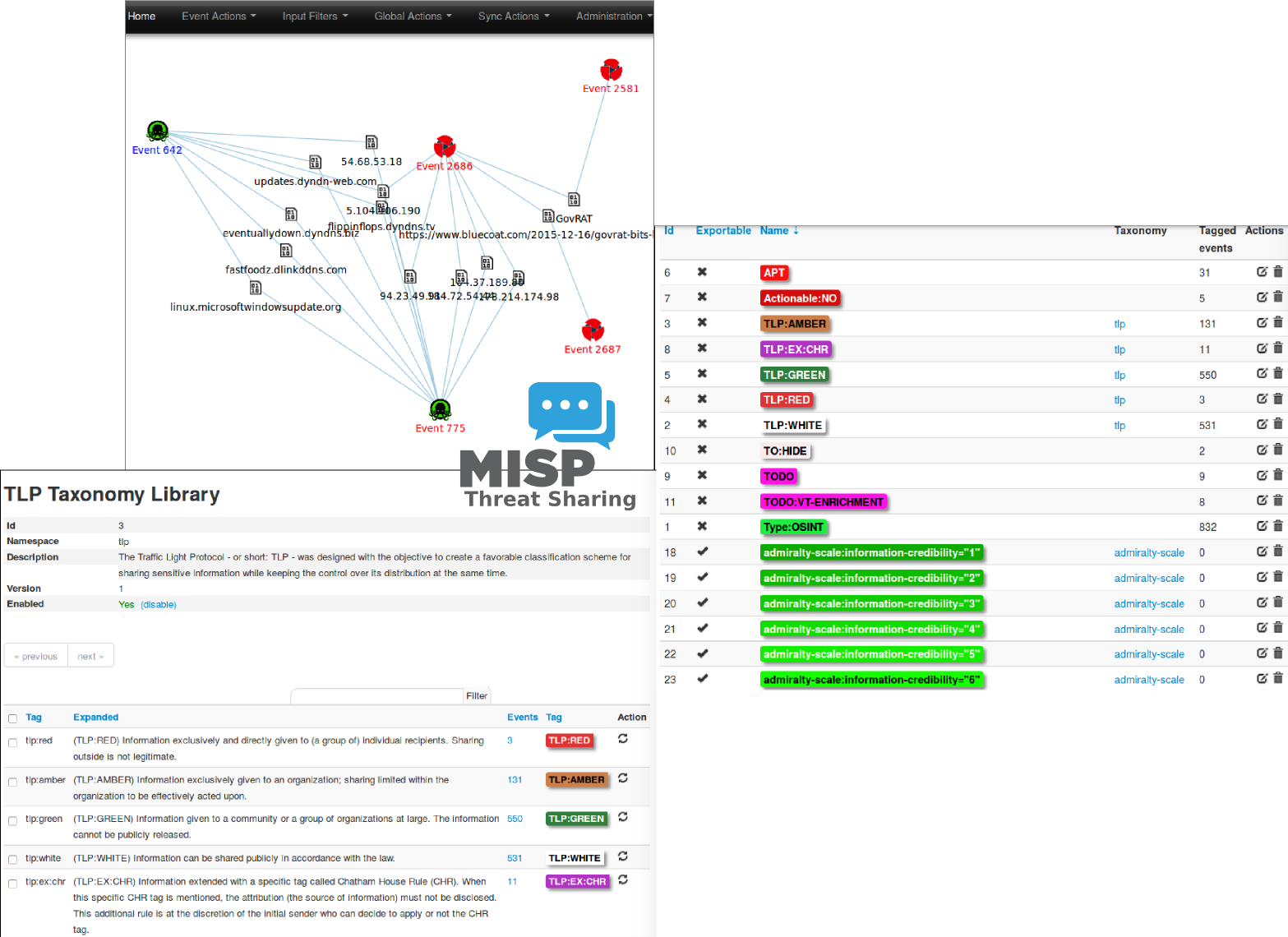
- Automatic correlation finding relationships between attributes and indicators from malware, attack campaigns or analysis. The correlation engine includes correlation between attributes and more advanced correlations like Fuzzy hashing correlation (e.g. ssdeep) or CIDR block matching. Correlation can also be enabled or event disabled per attribute.
- A flexible data model where complex objects can be expressed and linked together to express threat intelligence, incidents or connected elements.
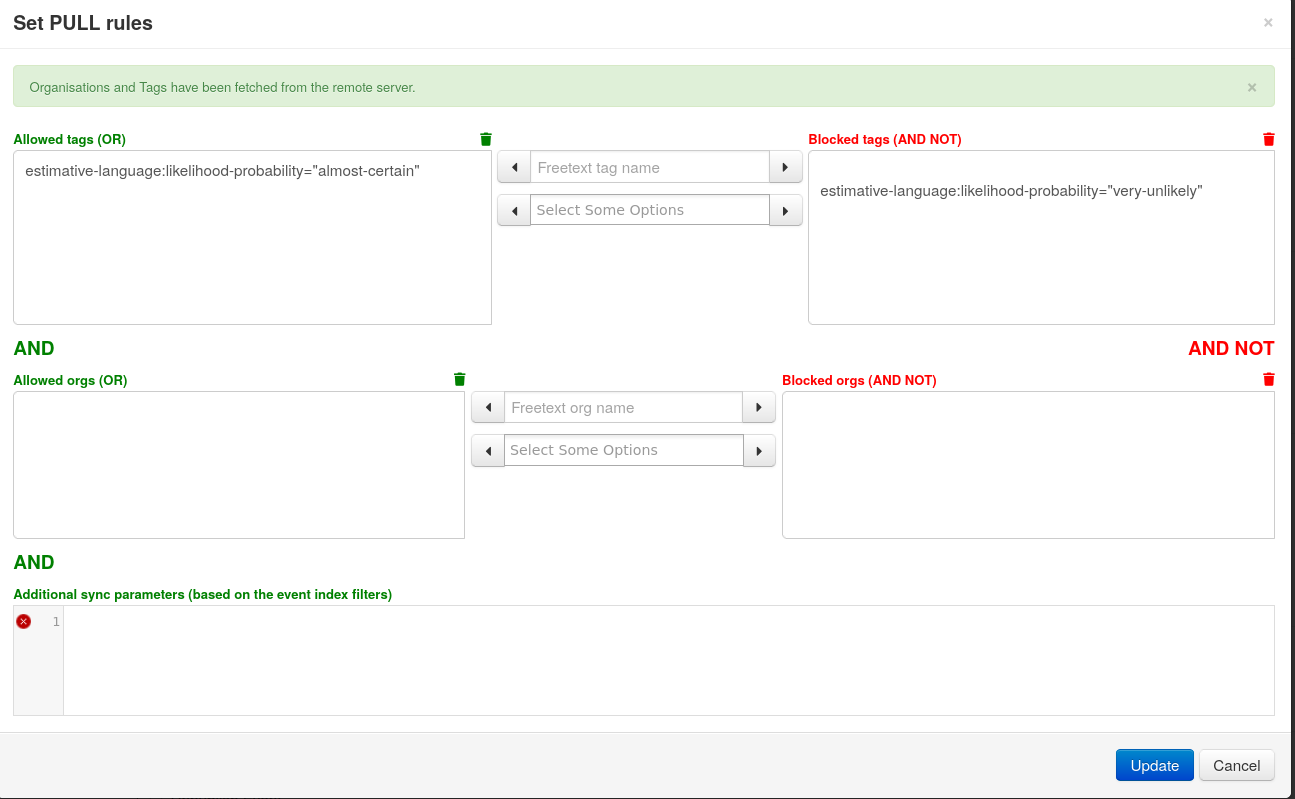
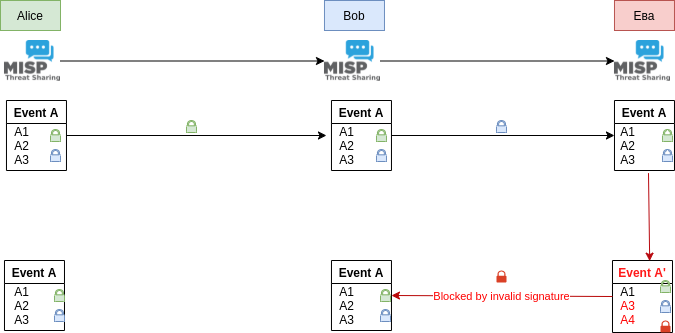
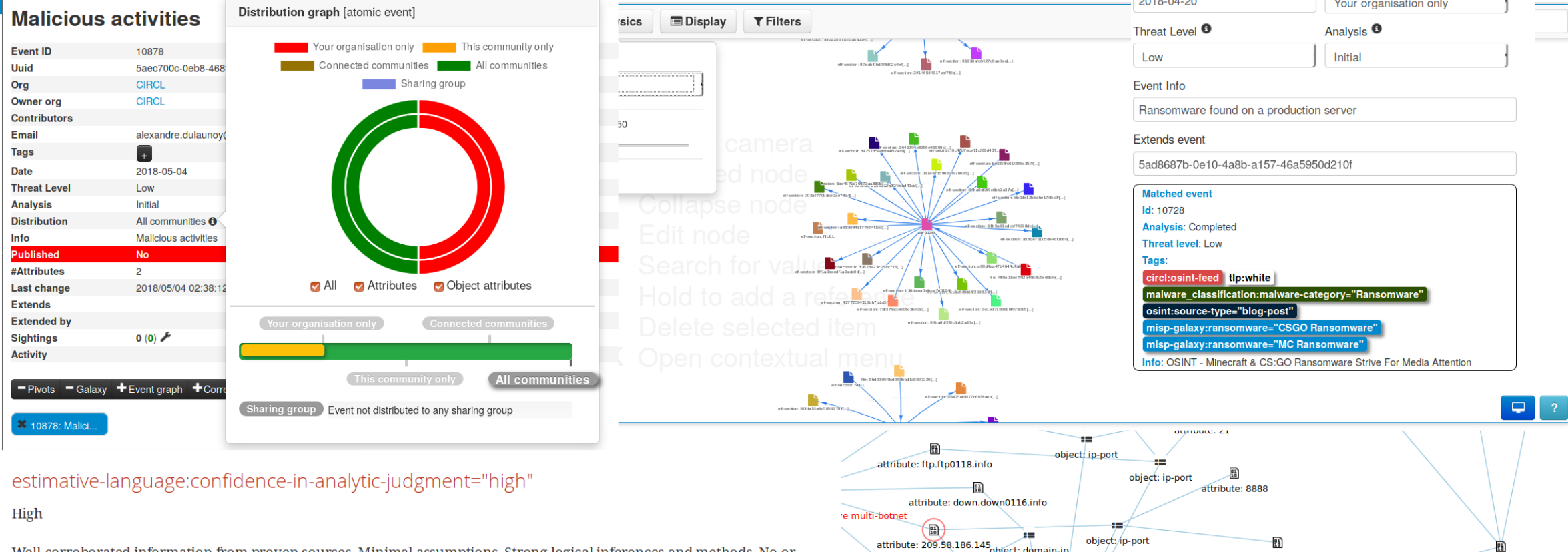
- Built-in sharing functionality to ease data sharing using different model of distributions. MISP can automatically synchronize events and attributes among different MISP instances. Advanced filtering functionalities can be used to meet each organization's sharing policy including a flexible sharing group capacity and an attribute level distribution mechanisms.
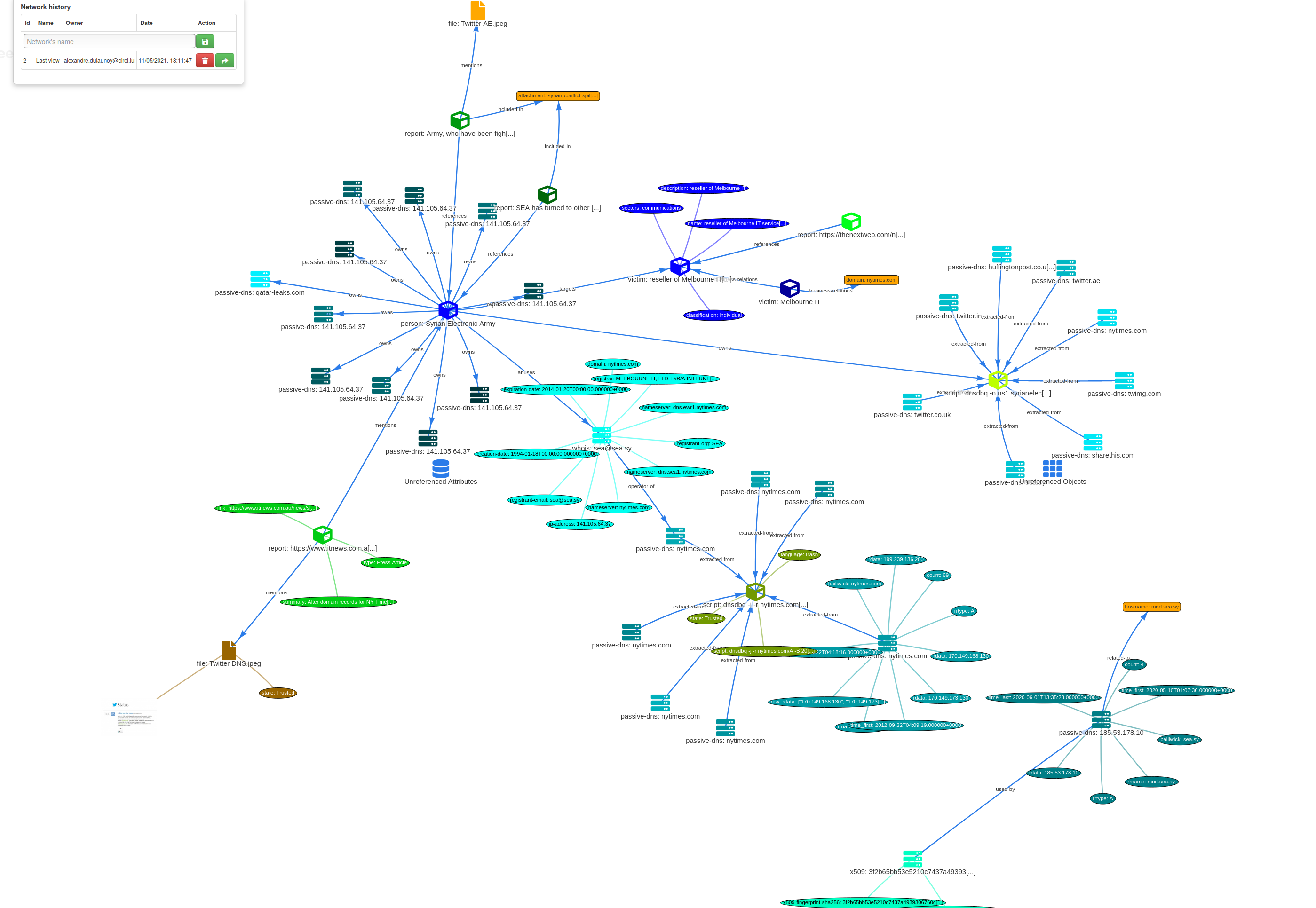
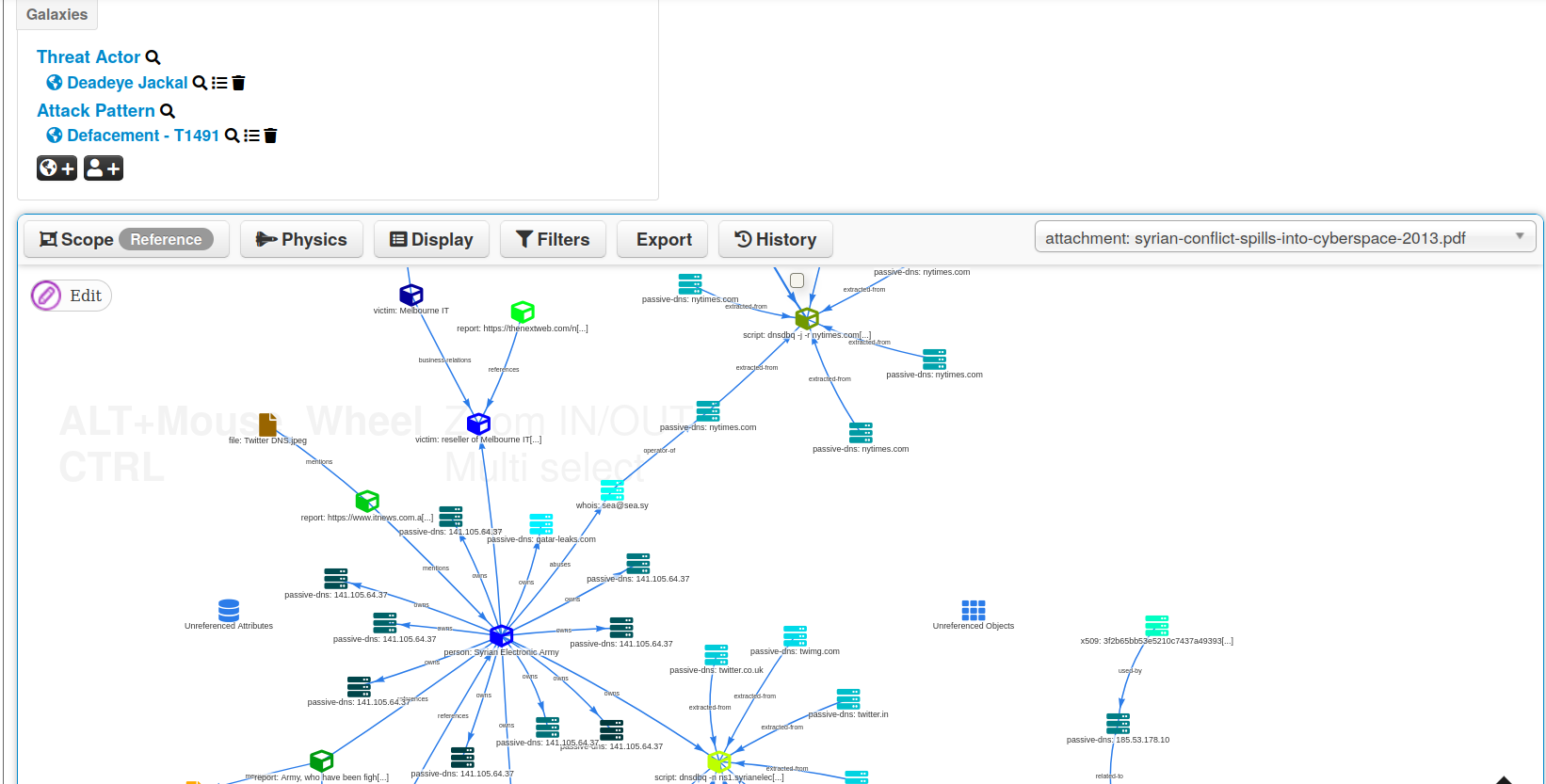
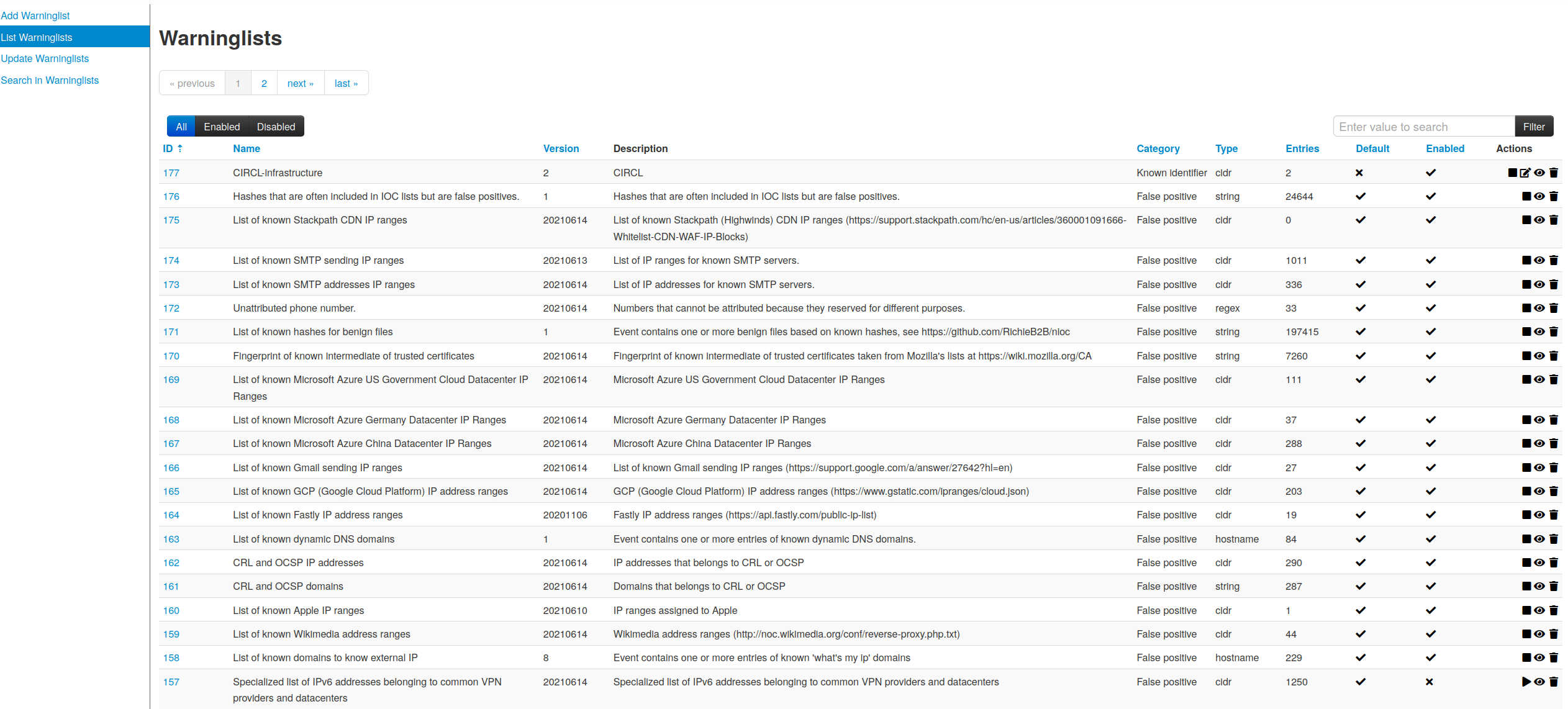
- An intuitive user-interface for end-users to create, update and collaborate on events and attributes/indicators. A graphical interface to navigate seamlessly between events and their correlations. An event graph functionality to create and view relationships between objects and attributes. Advanced filtering functionalities and warning lists to help the analysts to contribute events and attributes and limit the risk of false-positives.
- storing data in a structured format (allowing automated use of the database for various purposes) with an extensive support of cyber security indicators along fraud indicators as in the financial sector.
- export: generating IDS, OpenIOC, plain text, CSV, MISP XML or JSON output to integrate with other systems (network IDS, host IDS, custom tools), Cache format (used for forensic tools), STIX (XML and JSON) 1 and 2, NIDS export (Suricata, Snort and Bro/Zeek) or RPZ zone. Many other formats can be easily added via the misp-modules.
- import: bulk-import, batch-import, import from OpenIOC, GFI sandbox, ThreatConnect CSV, MISP standard format or STIX 1.1/2.0. Many other formats easily added via the misp-modules.
- Flexible free text import tool to ease the integration of unstructured reports into MISP.
- A gentle system to collaborate on events and attributes allowing MISP users to propose changes or updates to attributes/indicators.
- data-sharing: automatically exchange and synchronize with other parties and trust-groups using MISP.
- delegating of sharing: allows a simple pseudo-anonymous mechanism to delegate publication of event/indicators to another organization.
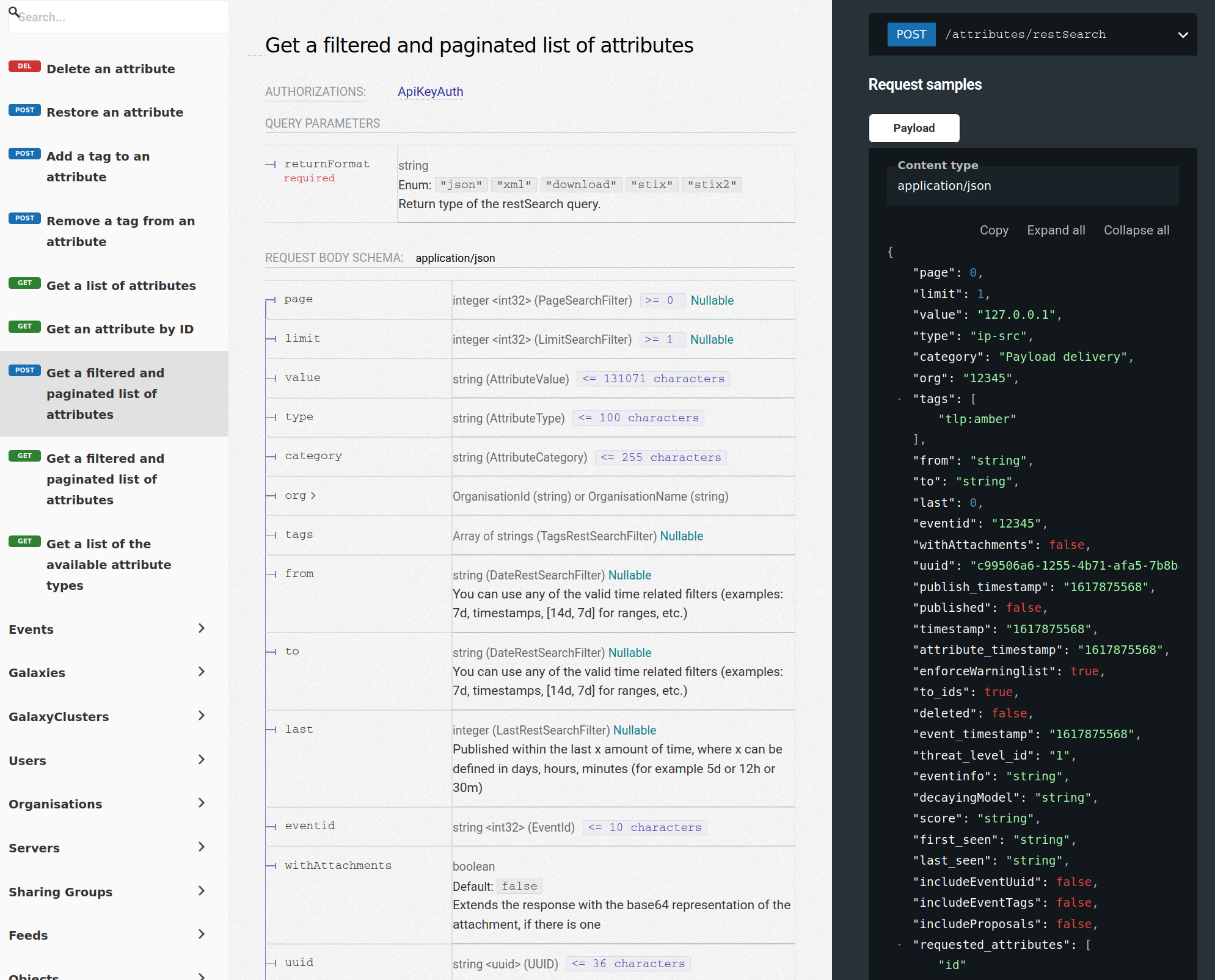
- Flexible API to integrate MISP with your own solutions. MISP is bundled with PyMISP which is a flexible Python Library to fetch, add or update events attributes, handle malware samples or search for attributes. An exhaustive restSearch API to easily search for indicators in MISP and exports those in all the format supported by MISP.
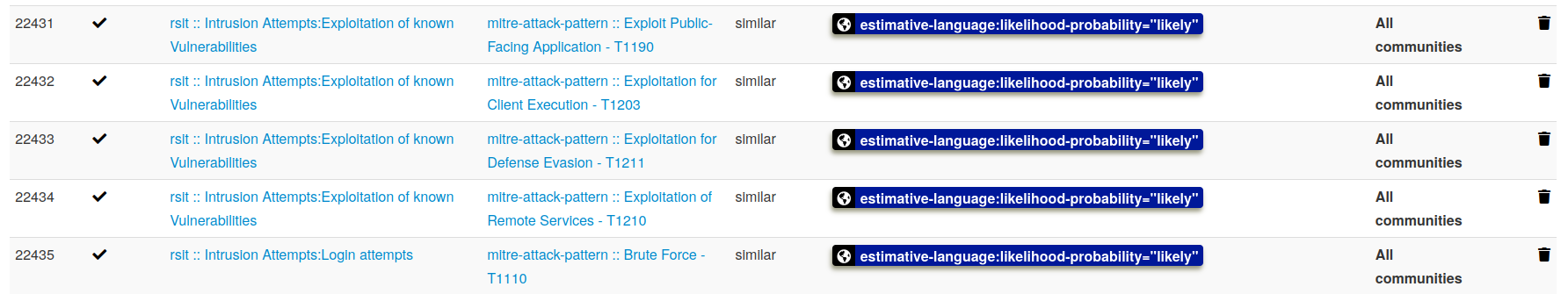
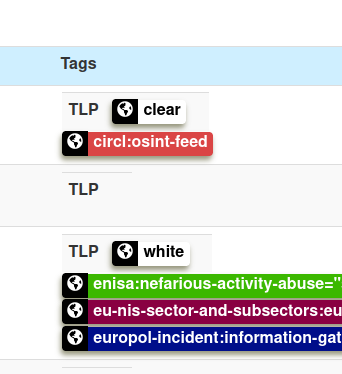
- Adjustable taxonomy to classify and tag events following your own classification schemes or existing classification. The taxonomy can be local to your MISP but also shareable among MISP instances.
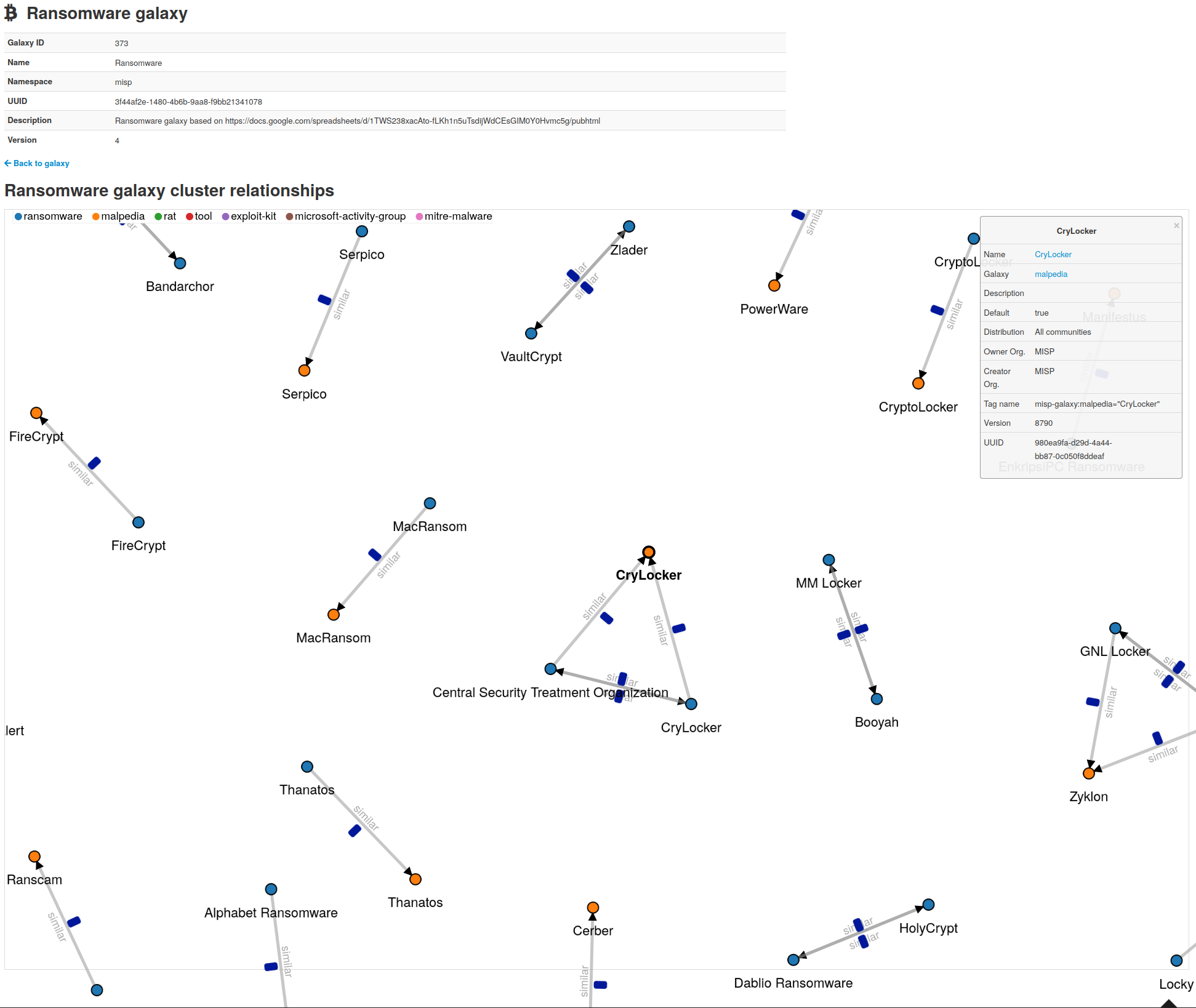
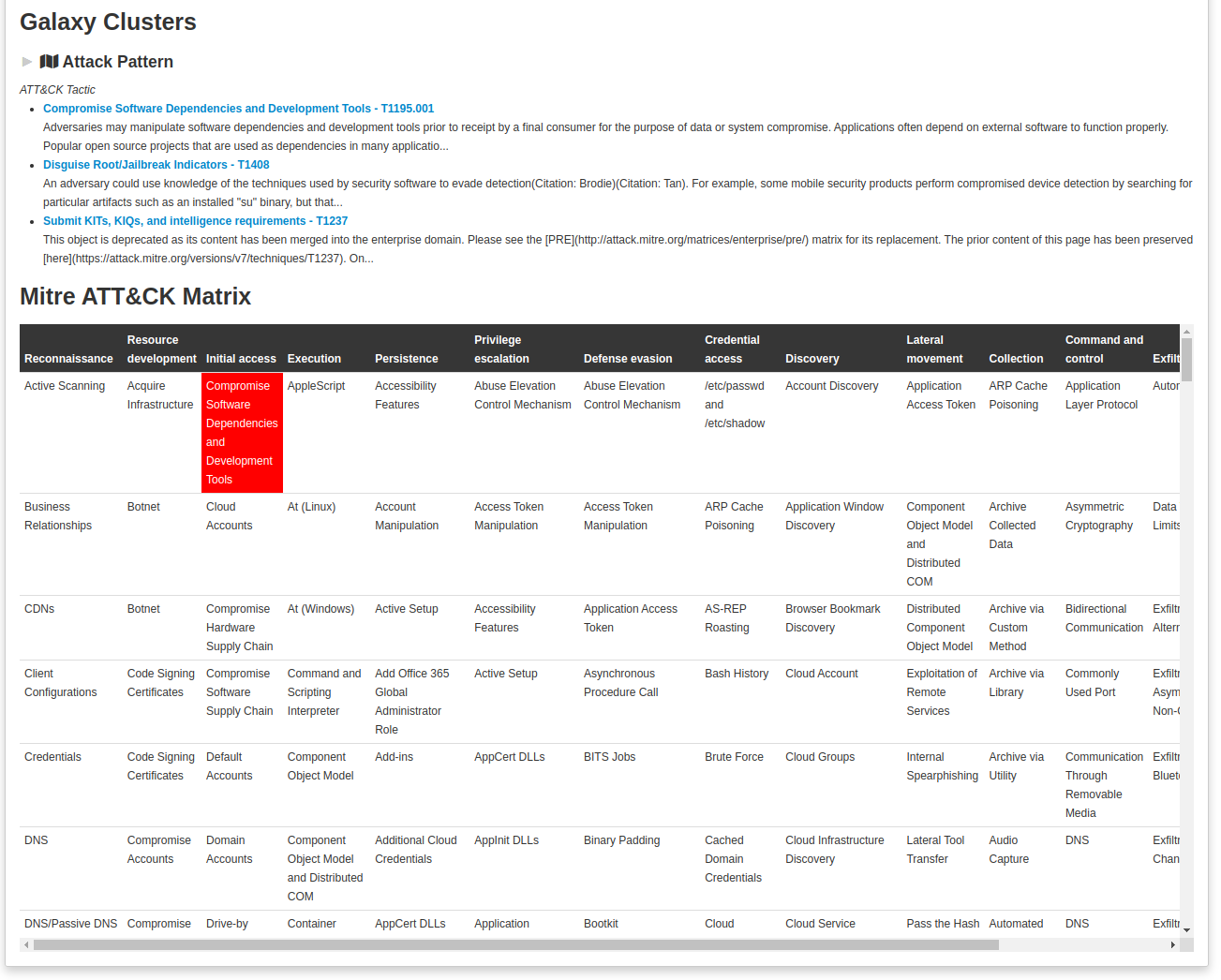
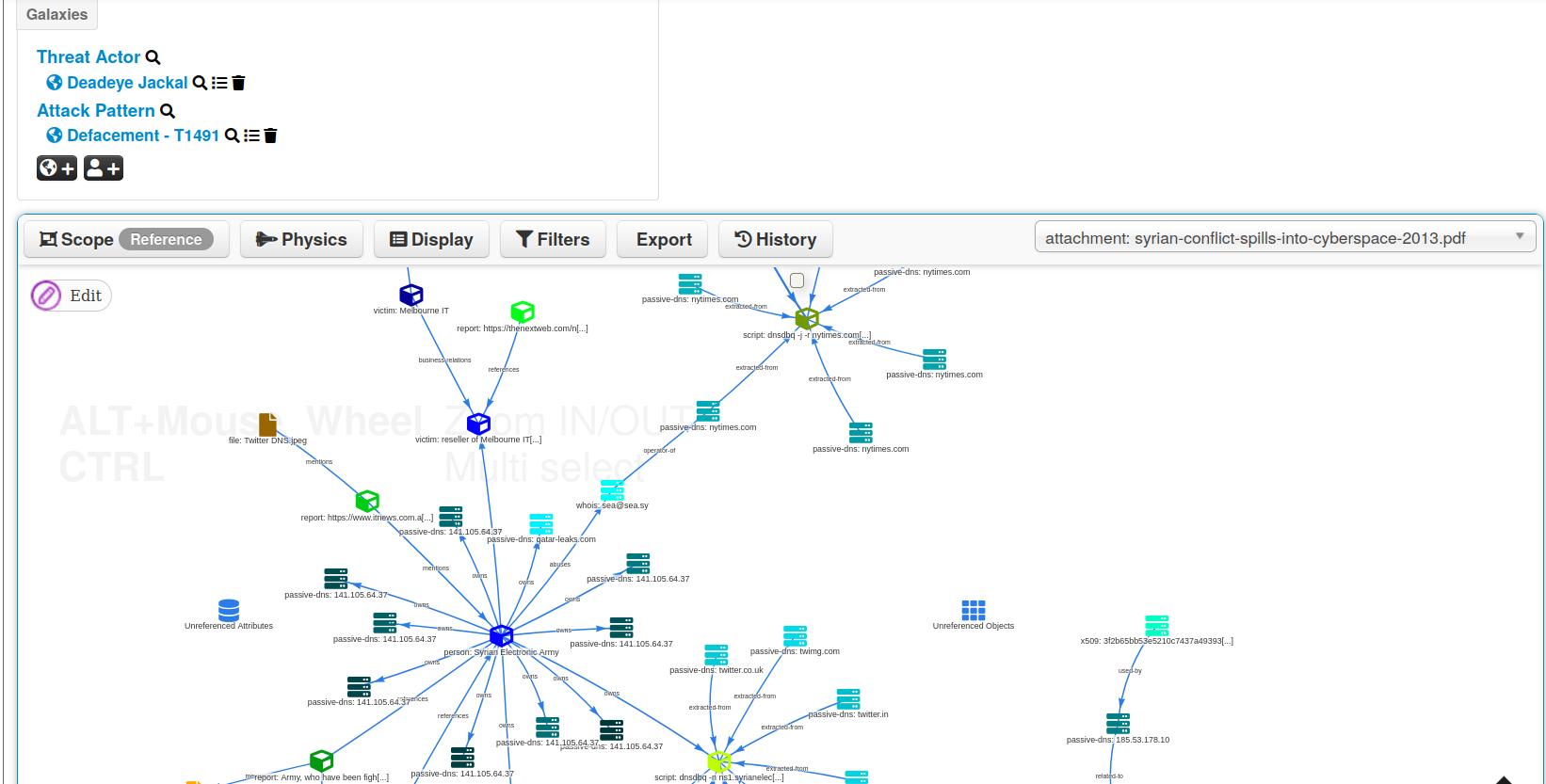
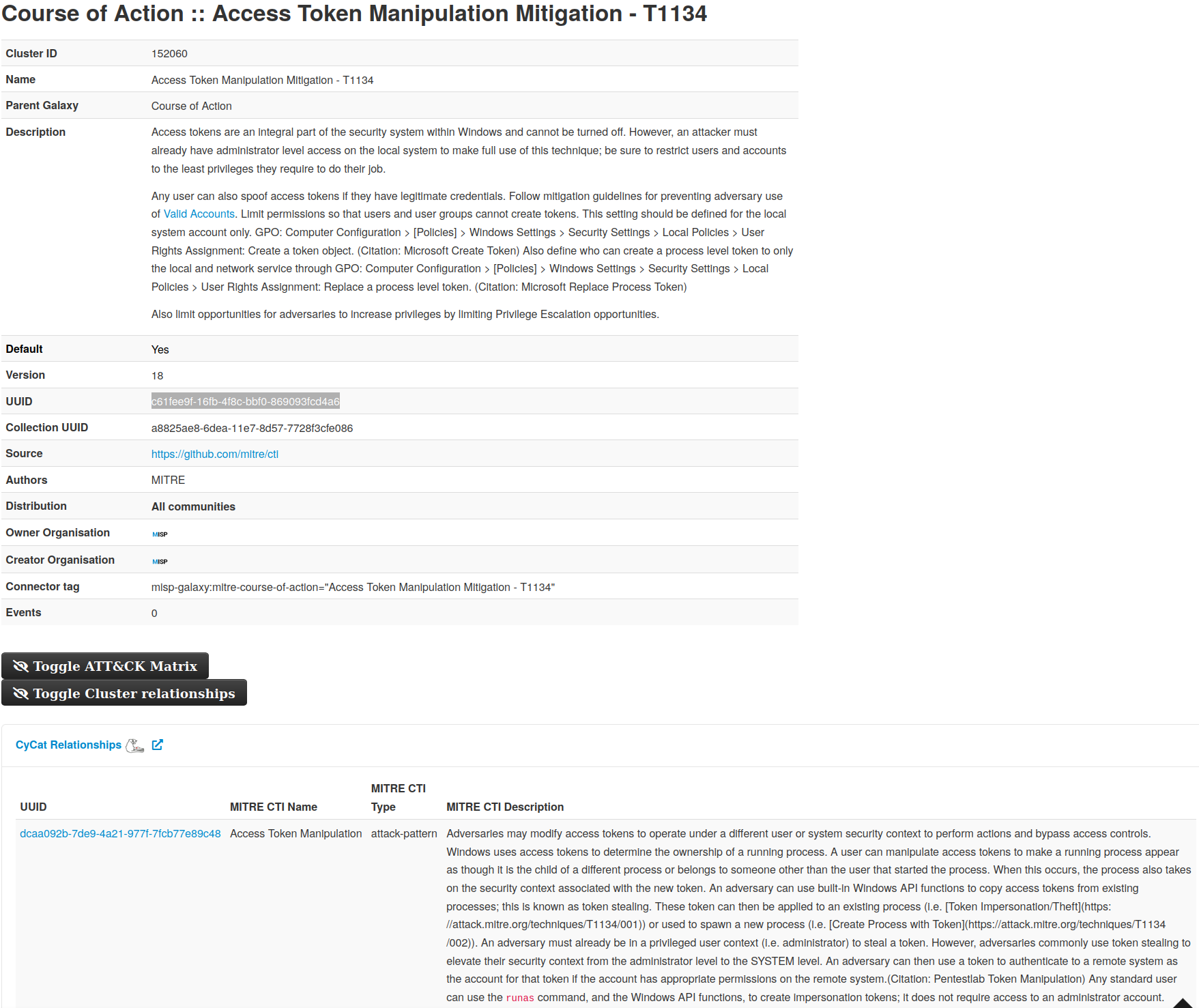
- Intelligence vocabularies called MISP galaxy and bundled with existing threat actors, malware, RAT, ransomware or MITRE ATT&CK which can be easily linked with events and attributes in MISP.
- Expansion modules in Python to expand MISP with your own services or activate already available misp-modules.
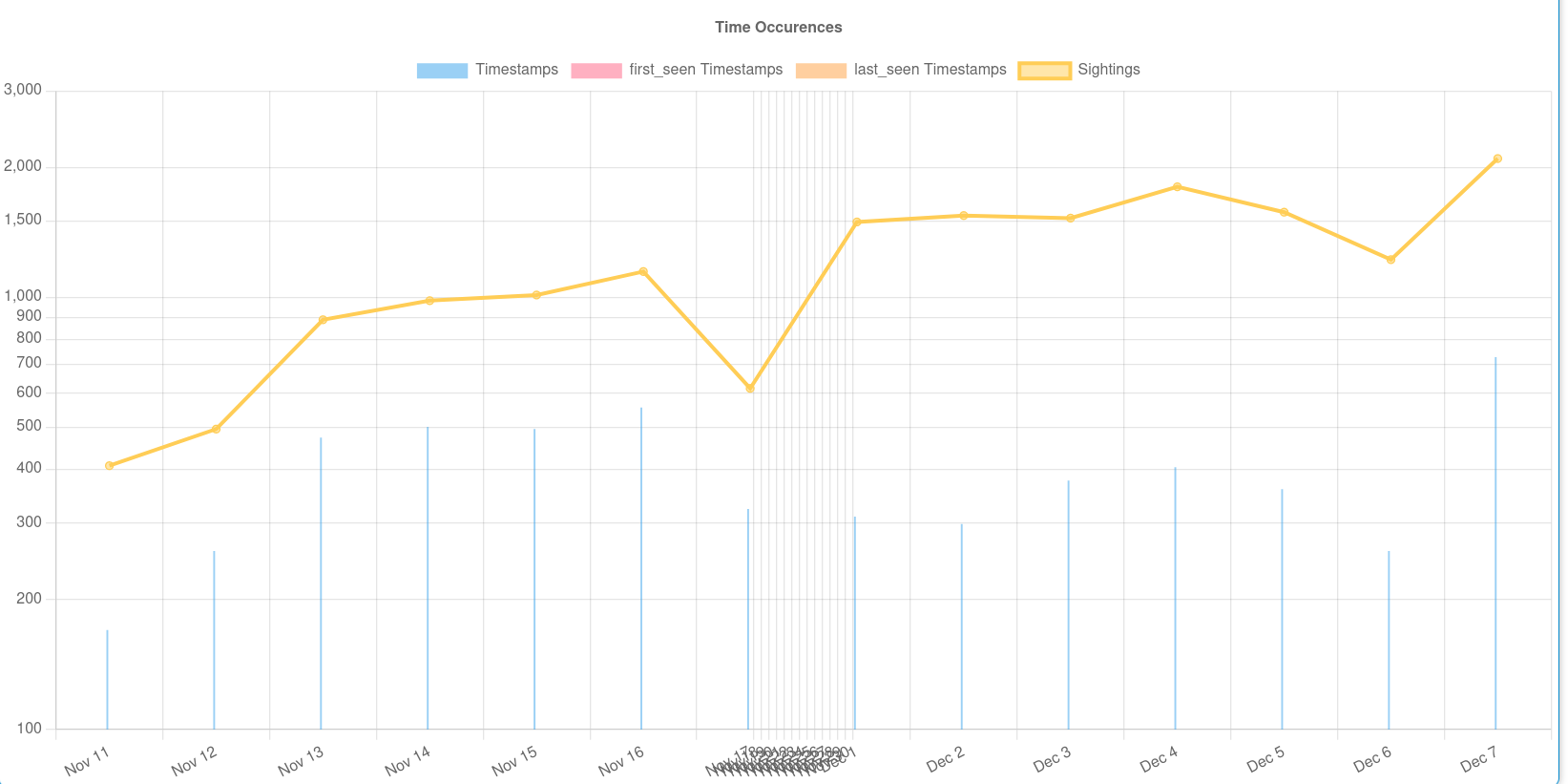
- Sighting support to get observations from organizations concerning shared indicators and attributes. Sighting can be contributed via MISP user-interface, API as MISP document or STIX sighting documents.
- STIX support: import and export data in the STIX version 1 and version 2 format.
- Integrated encryption and signing of the notifications via GnuPG and/or S/MIME depending on the user's preferences.
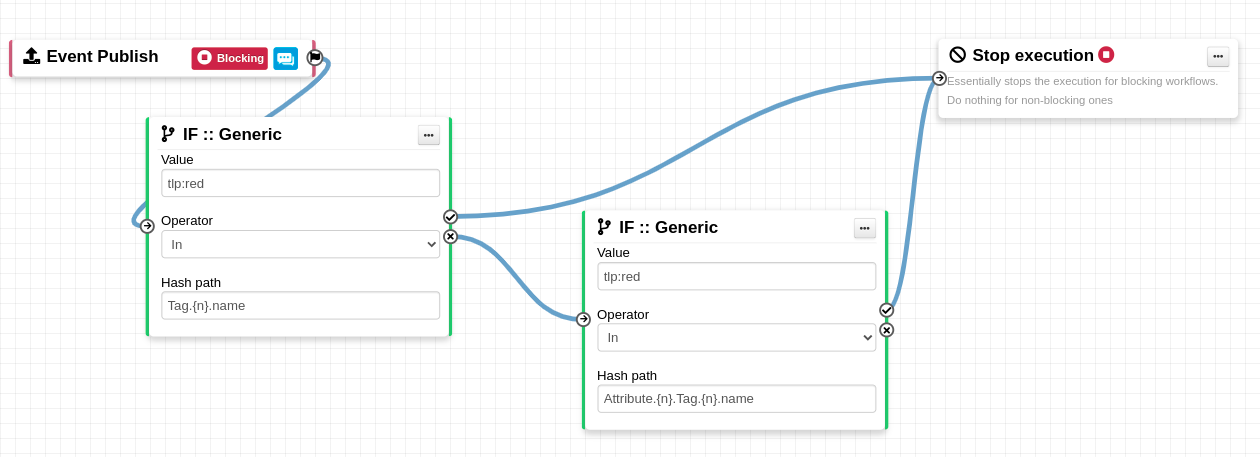
- Real-time publish-subscribe channel within MISP to automatically get all changes (e.g. new events, indicators, sightings or tagging) in ZMQ (e.g. misp-dashboard) or Kafka publishing.
Exchanging info results in faster detection of targeted attacks and improves the detection ratio while reducing the false positives. We also avoid reversing similar malware as we know very fast that other teams or organizations have already analyzed a specific malware.
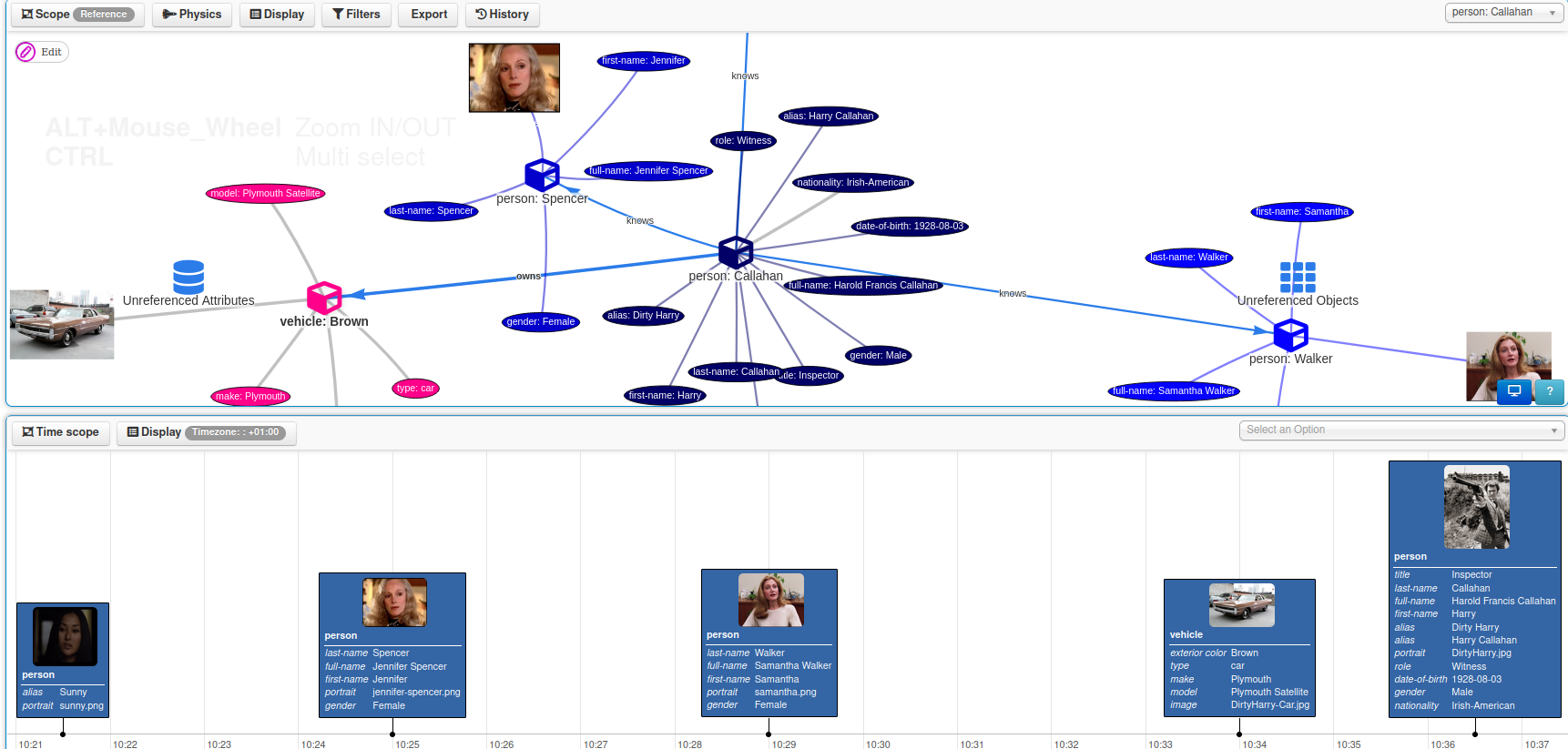
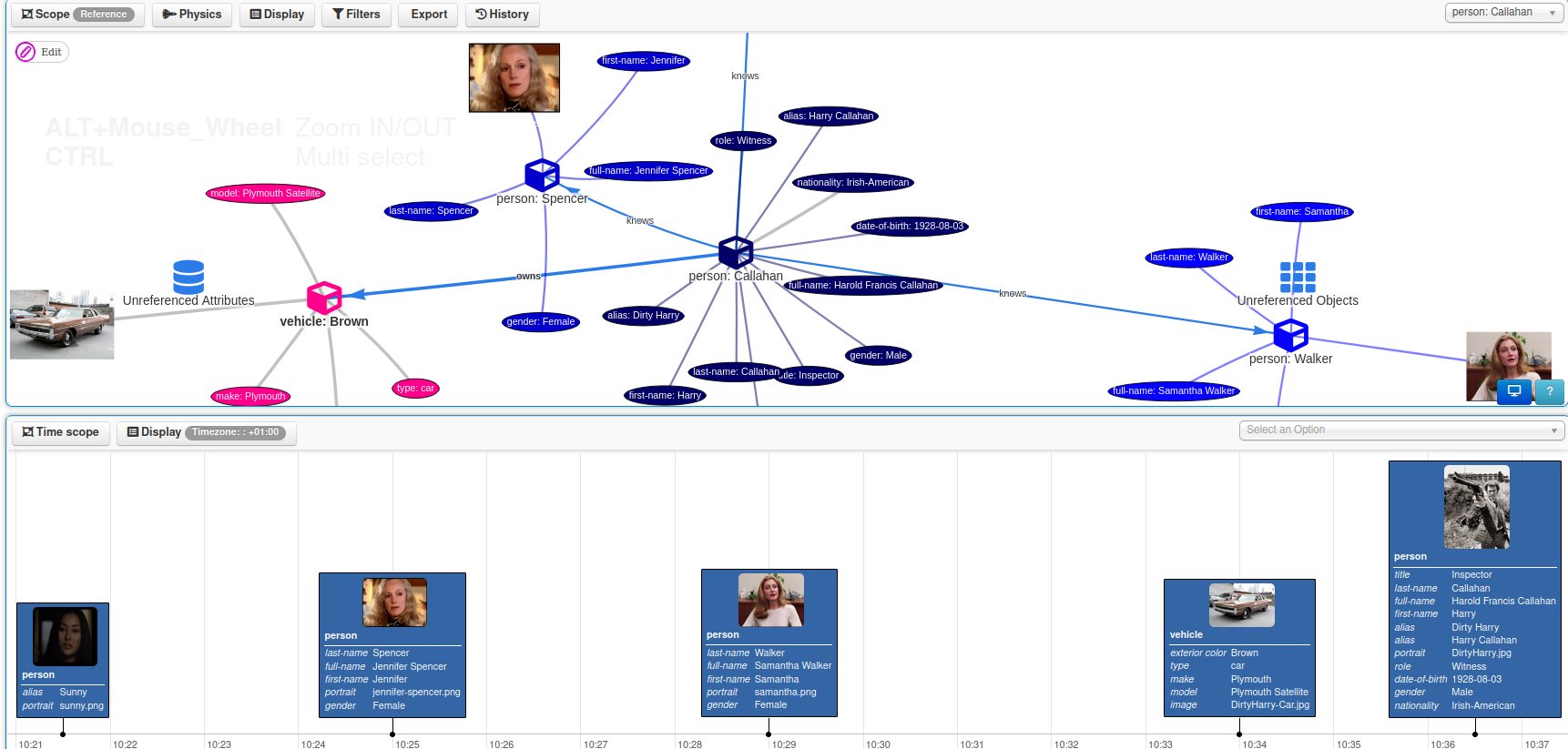
A sample event encoded in MISP:
Website / Support
Checkout the website for more information about MISP software, standards, tools and communities.
Information, news and updates are also regularly posted on the MISP project twitter account or the news page.
Documentation
MISP user-guide (MISP-book) is available online or as PDF or as EPUB or as MOBI/Kindle.
For the installation guide see the INSTALL or download section.
Contributing
If you are interested to contribute to the MISP project, review our contributing page. There are many ways to contribute and participate to the project.
Please see our Code of conduct.
Feel free to fork the code, play with it, make some patches and send us the pull requests via the issues.
Feel free to contact us, create issues, if you have questions, remarks or bug reports.
There is one main branch:
- 2.4 (current stable version): what we consider as stable with frequent updates as hot-fixes.
and features are developed in separated branches and then regularly merged into the 2.4 stable branch.
License
This software is licensed under GNU Affero General Public License version 3
- Copyright (C) 2012-2022 Christophe Vandeplas
- Copyright (C) 2012 Belgian Defence
- Copyright (C) 2012 NATO / NCIRC
- Copyright (C) 2013-2022 Andras Iklody
- Copyright (C) 2015-2022 CIRCL - Computer Incident Response Center Luxembourg
- Copyright (C) 2016 Andreas Ziegler
- Copyright (C) 2018-2022 Sami Mokaddem
- Copyright (C) 2018-2022 Christian Studer
- Copyright (C) 2015-2022 Alexandre Dulaunoy
- Copyright (C) 2018-2022 Steve Clement
- Copyright (C) 2020-2022 Jakub Onderka
For more information, the list of authors and contributors is available.




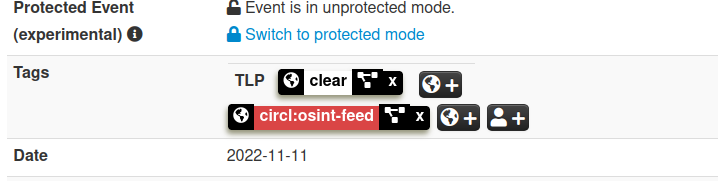
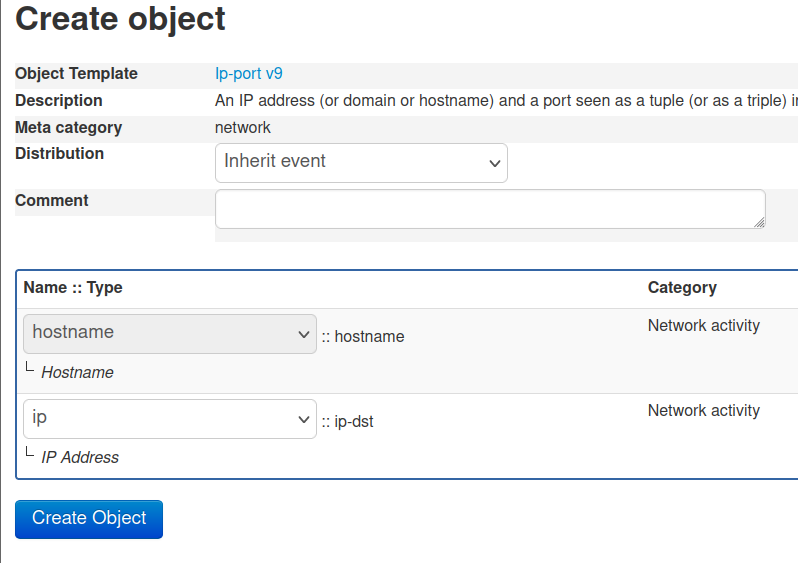
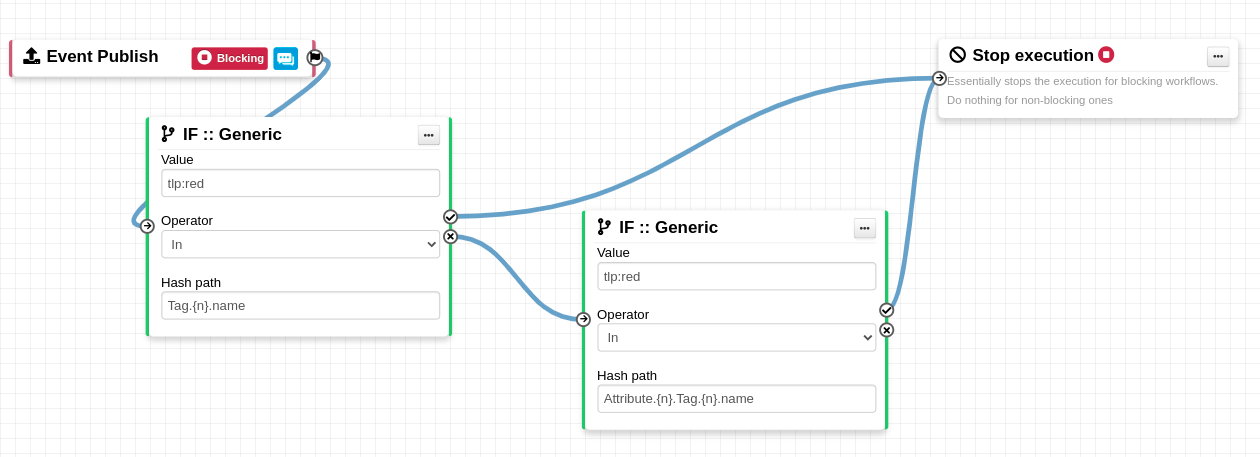
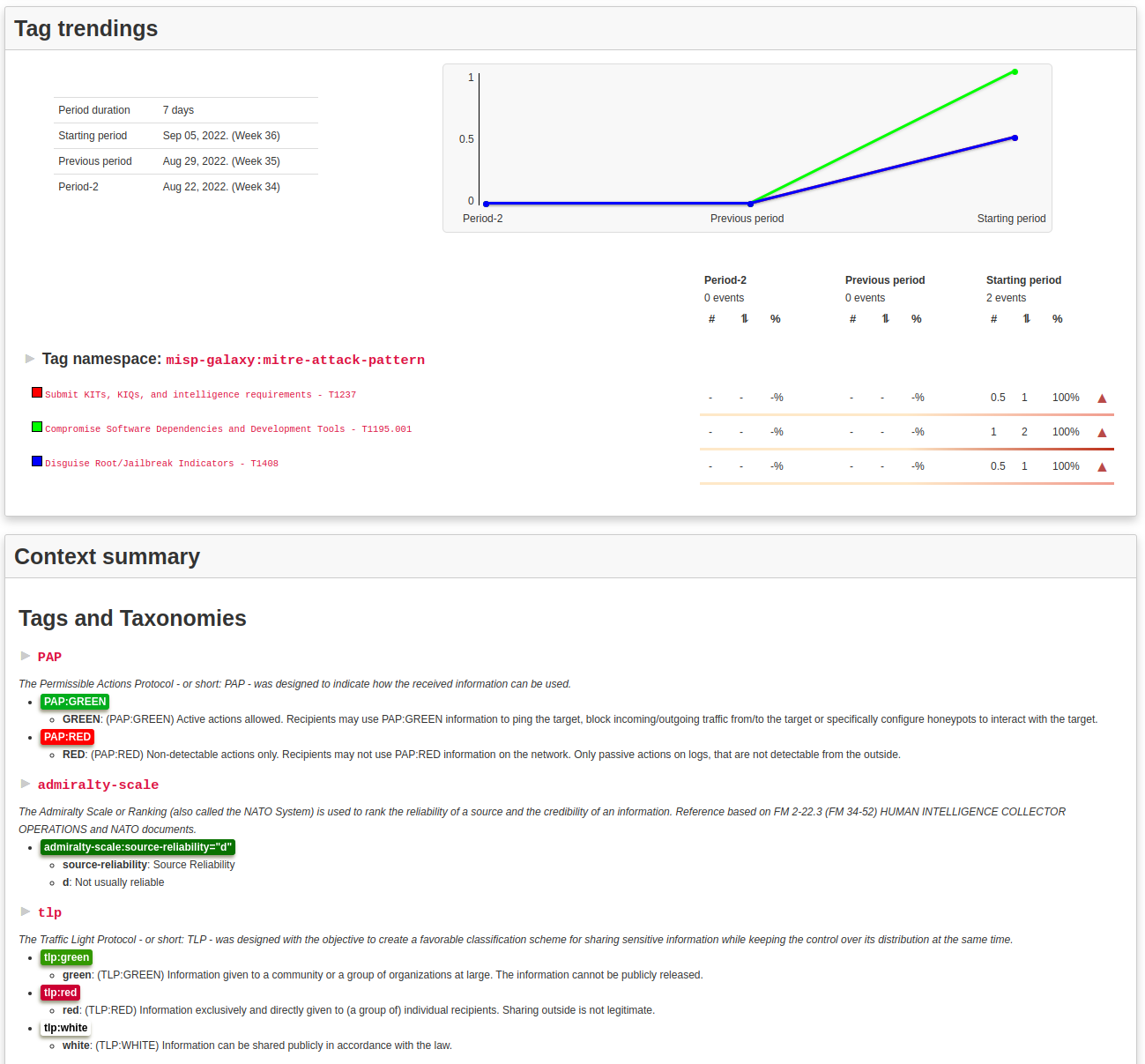






 and enable the feature.
and enable the feature.