Fix Major Security Vulnerability on PrestaShop Websites
🚀
CVE-2022-31101 detector and fixer!
A newly found exploit could allow remote attackers to take control of your shop
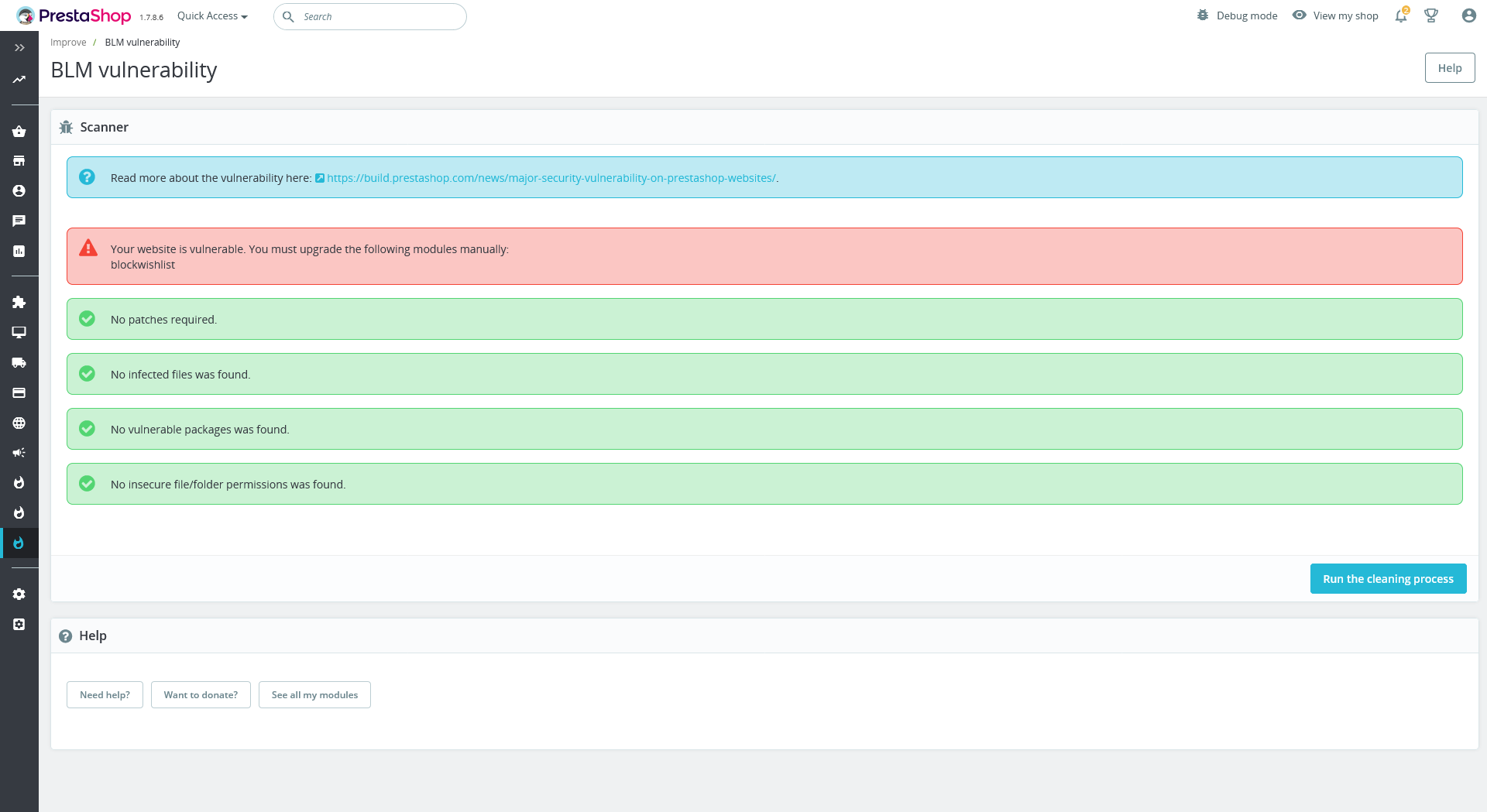
Read more about the vulnerability here: https://build.prestashop.com/news/major-security-vulnerability-on-prestashop-websites/.
Fix the backdoor
The module will make a security fix that strengthens the MySQL Smarty cache storage against code injection attacks.
Run this module on your shop to close the security issue.
Remove the malware
Many who have been hacked through this vulnerability have found that their payment gateway has been replaced with a fake one. If you are a victim of this attack, the module can probably recover your shop.
Run this module on your shop to recover from the attack.
How does the module work?
The module scans the files of your shop based on a pattern. This pattern is designed to find vulnerabilities and infected files known from the security issue.
The module will solve the problems automatically or tell you how to solve them manually.
Install the module
-
Download the latest version of the module: https://github.com/MathiasReker/blmvuln/releases/latest
-
Login into your shop's back office
-
Go to "Module Manager"
-
Click on "Upload a Module"
-
Upload and install the module
Usage
-
Open the module and click "Run the cleaning process".
-
After running the cleaning process, you can uninstall the module.
Compatibility
- PrestaShop 1.6.1+
- thirty bees 1.0.0+
- PHP 7.0+
Roadmap
See the open issues for a complete list of proposed features (and known issues).
Contributing
If you have a suggestion to improve this, please fork the repo and create a pull request. You can also open an issue with the tag "enhancement". Finally, don't forget to give the project a star! Thanks again!
License
It is distributed under the MIT License. See LICENSE for more information.